Ironkey was the first dedicated fully encrypted USB drive with hardware self-destruct mechanism after 10 failed attempts. Back in September 2007 I tested one of their first releases, without going the whole nine yards of destruction though. In the intervening years, IronKey as a company has made their way across the corporate landscape until they found a home in the Kingston portfolio.
Now one and a half decades on, I get to circle back to one of my earliest reviews for DRN and test out the newest iteration, the Kingston IronKey Virtual Privacy 50C.
What’s the big deal?
Kingston IronKey Vault Privacy 50 series are USB drives that provide business-grade security with FIPS 197 certified AES 256-bit hardware encryption in XTS mode, including safeguards against BadUSB with digitally-signed firmware and against Brute Force password attacks. The encrypted storage is entirely under the user’s physical control without reliance on internet or cloud services to safeguard your data.
Why is that important? Because data is valuable, information is king. In Australia we have recently had the high profile data breaches of Optus and Medibank. On a broader stage, LastPass has suffered a catastrophic breach to parts of their user database. Taking some of these security measures back into your own hands does not sound so silly after all.
And if you are wondering what BadUSB is, in a nutshell, it is an attack that exploits an inherent vulnerability in USB firmware. Such an attack reprograms a USB device, causing it to act as a human interface device; once re-engineered, the USB device is used to discreetly execute commands or run malicious programs on the victim’s computer.
The case for hardware encrypted storage
Many years and many job positions ago, I was tasked with providing a secure storage capacity to some staff doing a sensitive investigation into companies potentially doing bad things for financial gains and market share. Surprise!
The brief was simple. Three staff members will be travelling around the globe for extended periods, without returning to base. Each will all have a laptop running Windows 98 … yes, dear reader, let that sink in. I had to create a user friendly but highly secure storage space per device. At least one staff had a background of “higher security”, and the other two, let’s just leave it as layman. Very. I was given three weeks to figure it out and a princely budget of a couple of coffees – instant not espresso.
Yes I figured it out, worked my magic, taught the users, dotted every i and crossed every t before they went on their few months of travel and investigations on company dime. When they came back, I am debriefing and sanitising their non-SOE machines, what do I find? Not a single person bothered to secure their data, not a single byte of it. Why? Because ultimately it required them to take the extra voluntary step to enable the encrypted partition.
Moral of the story? Don’t trust users. Not even if they can talk the talk because and damn well aware of the need for that investigation. Simply because if it is not enforced by default, chances are everyone will take the path of least work and resistance. Not surprisingly it was a nice junket with little outcome.
Why do I tell this story? Because if I had the IronKey technology back then, I would have been able to enforce levels of security that give the users no other choice but to jump through the hoops.
First Impressions
It is a bit of a shame i don’t have the original IronKey anymore, it failed after a long service life with me. I suspect someone actually tried to access it and failed.
In contrast to the blocky brushed metal rectangular hunk that was the original IronKey I reviewed, the Kingston IronKey VP50C (IKVP50C) is smaller, curved edges and a metallic finish. I note in my original review that the height of the IronKey was an issue with stacked USB ports. Although this configuration is less common now with ultra slim notebooks being the norm, the width can still be an issue. That said is it not unique to the IKVP50C, standard sized USB drive will have similar challenges.
Again whilst the original IronKey felt heavier than usual back then, the weight of the IPVP50C does not register much in the way of difference to current day generations of USB drives.
Setup
Onboard the VP50C are executables to decrypt your drive. There is support for Windows and Mac (specific version will be documented later). On Windows you simply run the executable to start the device initialisation, no installer required.
On Windows, there is a caveat of needing two consecutive drive letters to be available. This is firstly for the unsecure read-only partition where the executables reside. The second drive letter is for mounting the encrypted partition once successful authentication is completed.
First up you set your preferred language, no brainer there. Then of course there is the obligatory EULA.
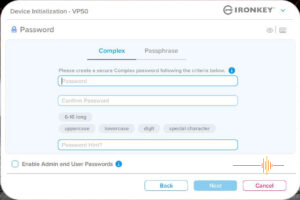
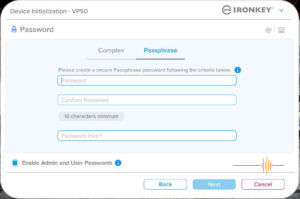
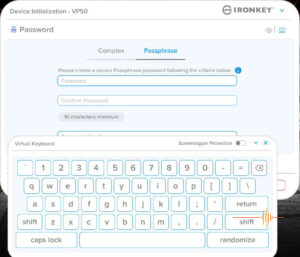
The next step is the meaty part where you set up your password. The interface gives you the option of creating either a Complex password or a Passphrase.
What the difference?
Complex password is set to be six to sixteen characters long, requiring a mix of uppercase, lowercase, digit and special character.
Passphrase has a 10 characters minimum.
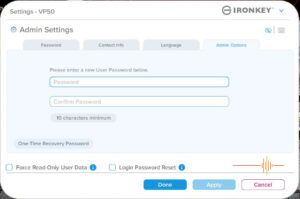
In the same dialogue box, you can tick the box to enable admin and user passwords.
To defeat keyloggers, there is a built-in virtual keyboard with the option of screenlogger protection. You can also randomise the keyboard for an added level of security.
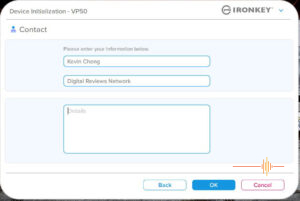
The last step is to put in your name, company and any details pertinent to facilitate the safe return of the IronKey.
In Use
The VP50C works just like any other USB drive once the secure partition is decrypted. The great part is that it forces a behaviour from the user in line with security policies.
In numerous organisations that I have worked in (or for), USB drive policies are extremely common. Their convenience makes it a glaring security issue which is why IronKey exists.
When the IronKey software is launched, you have the option to login as a user or administrator. There is also the read-only option as well as a tick box.
The performance is on par with other flash drives I have tested in recent times, USBDeview is giving me about 169 MB/sec write speed and 303 MB/sec read speed.
Other Features
There is nothing more dangerous than a user who thinks they know everything, and forgetting their passwords would rank right up there with writing it on a piece of paper and sticking it under the keyboard.
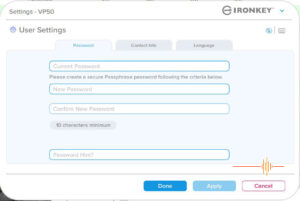
One of the key features of the VP50C is the ability for the administrator to reset the password.
This does require prior planning as this is enabled at device initialisation. If you didn’t enable this feature, the no, you can’t magically get into the IronKey to reset the password that the user has forgotten.
As an administrator of the IronKey, you can either reset the user’s password, or create a one time password to get in.
Lastly, the drive is also stated to be waterproof up to 4 feet which is a nice feature to have.
This message will self destruct …
Not quite 007.
The VP50C is preconfigured to allow 10 tries to login. When you have failed seven times already, an error message will indicate there is three attempts left.
Depending on how your VP50C is initialised, there are a few outcomes when you failed 10 times. Unlike the first generation IronKey I tested, this one will not self-destruct.
If your drive is in single user, no admin mode, then it gets crypto-erased and that’s the end of what data you have stored on it.
If you have the admin/user mode enabled, then locking out the user login count will not erase the drive. At this point you can unlock it with the admin password. However if you also failed with ten attempts using the admin password, again the drive will be crypto-erased.
Failing the one-time recovery password to the tune of ten attempts will keep the data, but the only way back in is with the admin password.
Gripes
I found the device initialisation to be more complicated than it needed to be. It can be clearer in getting the users to make a choice between complex password or a passphrase.
Also the checkbox for enabling an admin password was easy to miss.
Conclusions
I would argue that the device initialise process can be smoother. It wasn’t something I could do without giving it a bit of attention. At least in my case, it was a once off process rather than having to mass deploy.
I absolutely applaud hardware encrypted USB drives and it needs to be more mainstream. Kingston has made it simple for those who are privacy security conscious, for those who hasn’t thought about it, it’s always a good time to form new good habits.
The Kingston IronKey VP50C is available in 8GB and up to 256GB, in both USB-A and USB-C connectors. Prices ranges from AUD$80 up to about $400 for the largest capacity.
DRN would like to thank Kingston for providing the review unit.
Specifications
Interface: USB 3.2 Gen 1
Capacities: 8GB, 16GB, 32GB, 64GB, 128GB, 256GB
Connector: Type-A Type-C
Speed: USB 3.2 Gen 1
8GB – 128GB: 250MB/s read, 180MB/s write
256GB: 230MB/s read, 150MB/s write
USB 2.0
8GB – 256GB: 30MB/s read, 20MB/s write
Dimensions: 77.9 mm x 21.9 mm x 12.0 mm
Waterproof: Up to 4 ft; IEC 60529 IPX8
Operating Temperature: 0°C to 60°C
Storage Temperature: -20°C to 85°C
Compatibility: USB 3.0/USB 3.1/USB 3.2 Gen 1
Warranty/support: Limited 5-year warranty, free technical support
Compatible with: Type-A
Windows 11, 10, macOS® 10.15.x – 13.x
Type-C
Windows 10, 8.1, 8, macOS (v. 10.14.x – 11.x)